I don’t know if this topic is in the correect forum, feel free to move if not
on my laptop running 15.5 and KDE using user1 I attach my USB disk or stick and I can access easily to its content.
when I switch to user2 I cannot access to my USB disk or stick, even if I remove and attach again.
how can I have my USB stick or disk available to all the users?
Like all file systems mounted for use by all users, root can mount it on a mount point accessible by all. Either by using the mount command (maybe helped by configuring the lot of parameters in /etc/fstab, or maybe “always” (from boot till shutdown), by configuring it in /etc/fstab.
@pier_andreit Hi, it’s all about file permissions and ownership/groups.
See here: https://doc.opensuse.org/documentation/leap/security/html/book-security/sec-sec-file-management.html
You will see a note “Important: Test permission changes”
There are so many ways this can be done…
Complicating factors are:
- when the file system is already mounted through the desktop, the mount point is dedicated to the user (and other users have no normal access to that);
- when the file system is non-Linux (which is often the case with spontanious by an end-user connected mass-storage device), the ownership and permissions are faked and unchangeable.
@hcvv for 1. I suspect if it’s just one USB device, based on the lsusb output, one could craft a udev rule to mount somewhere on demand, or like you indicated, a fstab entry with nofail?
That is what I would prefer (as suggested above). Udev rules are more complicated for most people.
The real solution is of course that the original user does a “save remove” and disconnects it before he gives the device to another human. That would also be the better way of living in a security aware environment. Not leaving your data lying around (or in this case even connected to the computer) for others.
It may be that many Linux users coming from an MS Windows environment do so (partly) because of more security. I find it always humorous to see how they then stumble into security barriers and then, without even contemplating about the security logic of them, immediately want to do away with such restrictions. Yes, “security” and “easy of use” are to ends of the balance.
Post output of
findmnt -u
when you are doing it.
And once more after you have done this.
manythanks, but in this case I have many users with theyr settings and tenth of usb sticks so I my better way of live is to have everything accessible to all the users regardless to security and with much regard to ease of use, is there a way to have this?
manythanks, I did what you asked, if I safely remove, system asks me root password, detach and attach again it works, is it possible to do it without be asked for root password?
here is the output of command after switched to user2, after safely removed in user2 with root password, after attached again in user2
attached and mounted in user pla&st
switched user to user pla
pla@localhost:~> findmnt -u
TARGET SOURCE FSTYPE OPTIONS
/ /dev/nvme0n1p4
│ ext4 rw,relatime
├─/proc
│ proc proc rw,nosuid,nodev,noexec,relatime
│ └─/proc/sys/fs/binfmt_misc
│ systemd-1
│ autofs rw,relatime,fd=30,pgrp=1,timeout=0,minproto=5,maxproto=5,direct,pipe_ino=24260
├─/sys sysfs sysfs rw,nosuid,nodev,noexec,relatime
│ ├─/sys/kernel/security
│ │ securityfs
│ │ securityfs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/fs/cgroup
│ │ tmpfs tmpfs ro,nosuid,nodev,noexec,size=4096k,nr_inodes=1024,mode=755,inode64
│ │ ├─/sys/fs/cgroup/unified
│ │ │ cgroup2
│ │ │ cgroup2
│ │ │ rw,nosuid,nodev,noexec,relatime,nsdelegate
│ │ ├─/sys/fs/cgroup/systemd
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,xattr,name=systemd
│ │ ├─/sys/fs/cgroup/misc
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,misc
│ │ ├─/sys/fs/cgroup/freezer
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,freezer
│ │ ├─/sys/fs/cgroup/blkio
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,blkio
│ │ ├─/sys/fs/cgroup/cpu,cpuacct
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,cpu,cpuacct
│ │ ├─/sys/fs/cgroup/rdma
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,rdma
│ │ ├─/sys/fs/cgroup/memory
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,memory
│ │ ├─/sys/fs/cgroup/net_cls,net_prio
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,net_cls,net_prio
│ │ ├─/sys/fs/cgroup/devices
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,devices
│ │ ├─/sys/fs/cgroup/perf_event
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,perf_event
│ │ ├─/sys/fs/cgroup/pids
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,pids
│ │ ├─/sys/fs/cgroup/hugetlb
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,hugetlb
│ │ └─/sys/fs/cgroup/cpuset
│ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,cpuset
│ ├─/sys/fs/pstore
│ │ pstore pstore rw,nosuid,nodev,noexec,relatime
│ ├─/sys/firmware/efi/efivars
│ │ efivarfs
│ │ efivarfs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/fs/bpf
│ │ bpf bpf rw,nosuid,nodev,noexec,relatime,mode=700
│ ├─/sys/kernel/debug
│ │ debugfs
│ │ debugfs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/kernel/tracing
│ │ tracefs
│ │ tracefs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/fs/fuse/connections
│ │ fusectl
│ │ fusectl
│ │ rw,nosuid,nodev,noexec,relatime
│ └─/sys/kernel/config
│ configfs
│ configfs
│ rw,nosuid,nodev,noexec,relatime
├─/dev devtmpfs
│ devtmpfs
│ rw,nosuid,size=4096k,nr_inodes=1048576,mode=755,inode64
│ ├─/dev/shm
│ │ tmpfs tmpfs rw,nosuid,nodev,inode64
│ ├─/dev/pts
│ │ devpts devpts rw,nosuid,noexec,relatime,gid=5,mode=620,ptmxmode=000
│ ├─/dev/mqueue
│ │ mqueue mqueue rw,nosuid,nodev,noexec,relatime
│ └─/dev/hugepages
│ hugetlbfs
│ hugetlbfs
│ rw,relatime,pagesize=2M
├─/run tmpfs tmpfs rw,nosuid,nodev,size=4859812k,nr_inodes=819200,mode=755,inode64
│ ├─/run/media/pla6ST/backup7
│ │ /dev/sda1
│ │ fuseblk
│ │ rw,nosuid,nodev,relatime,user_id=0,group_id=0,default_permissions,allow_other,blksize=4096
│ ├─/run/user/1000
│ │ tmpfs tmpfs rw,nosuid,nodev,relatime,size=2429904k,nr_inodes=607476,mode=700,uid=1000,gid=100,inode64
│ │ ├─/run/user/1000/doc
│ │ │ portal fuse.portal
│ │ │ rw,nosuid,nodev,relatime,user_id=1000,group_id=100
│ │ └─/run/user/1000/gvfs
│ │ gvfsd-fuse
│ │ fuse.gvfsd-fuse
│ │ rw,nosuid,nodev,relatime,user_id=1000,group_id=100
│ └─/run/user/1002
│ tmpfs tmpfs rw,nosuid,nodev,relatime,size=2429904k,nr_inodes=607476,mode=700,uid=1002,gid=100,inode64
│ ├─/run/user/1002/doc
│ │ portal fuse.portal
│ │ rw,nosuid,nodev,relatime,user_id=1002,group_id=100
│ └─/run/user/1002/gvfs
│ gvfsd-fuse
│ fuse.gvfsd-fuse
│ rw,nosuid,nodev,relatime,user_id=1002,group_id=100
├─/home
│ /dev/nvme0n1p5
│ ext4 rw,relatime,data=ordered
├─/dati
│ /dev/nvme0n1p8
│ fuseblk
│ rw,nosuid,nodev,noexec,relatime,user_id=0,group_id=0,default_permissions,allow_other,blksize=4096
├─/boot/efi
│ /dev/nvme0n1p1
│ vfat rw,relatime,fmask=0022,dmask=0022,codepage=437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro
└─/tmp/.mount_ObsidiW6jN44
Obsidian-1.4.16.AppImage
fuse.Obsidian-1.4.16.AppImage
ro,nosuid,nodev,relatime,user_id=1000,group_id=100
pla@localhost:~>
================================================
safely removed in user pla and system asked me root password
pla@localhost:~> findmnt -u
TARGET SOURCE FSTYPE OPTIONS
/ /dev/nvme0n1p4
│ ext4 rw,relatime
├─/proc
│ proc proc rw,nosuid,nodev,noexec,relatime
│ └─/proc/sys/fs/binfmt_misc
│ systemd-1
│ autofs rw,relatime,fd=30,pgrp=1,timeout=0,minproto=5,maxproto=5,direct,pipe_ino=24260
├─/sys sysfs sysfs rw,nosuid,nodev,noexec,relatime
│ ├─/sys/kernel/security
│ │ securityfs
│ │ securityfs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/fs/cgroup
│ │ tmpfs tmpfs ro,nosuid,nodev,noexec,size=4096k,nr_inodes=1024,mode=755,inode64
│ │ ├─/sys/fs/cgroup/unified
│ │ │ cgroup2
│ │ │ cgroup2
│ │ │ rw,nosuid,nodev,noexec,relatime,nsdelegate
│ │ ├─/sys/fs/cgroup/systemd
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,xattr,name=systemd
│ │ ├─/sys/fs/cgroup/misc
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,misc
│ │ ├─/sys/fs/cgroup/freezer
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,freezer
│ │ ├─/sys/fs/cgroup/blkio
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,blkio
│ │ ├─/sys/fs/cgroup/cpu,cpuacct
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,cpu,cpuacct
│ │ ├─/sys/fs/cgroup/rdma
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,rdma
│ │ ├─/sys/fs/cgroup/memory
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,memory
│ │ ├─/sys/fs/cgroup/net_cls,net_prio
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,net_cls,net_prio
│ │ ├─/sys/fs/cgroup/devices
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,devices
│ │ ├─/sys/fs/cgroup/perf_event
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,perf_event
│ │ ├─/sys/fs/cgroup/pids
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,pids
│ │ ├─/sys/fs/cgroup/hugetlb
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,hugetlb
│ │ └─/sys/fs/cgroup/cpuset
│ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,cpuset
│ ├─/sys/fs/pstore
│ │ pstore pstore rw,nosuid,nodev,noexec,relatime
│ ├─/sys/firmware/efi/efivars
│ │ efivarfs
│ │ efivarfs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/fs/bpf
│ │ bpf bpf rw,nosuid,nodev,noexec,relatime,mode=700
│ ├─/sys/kernel/debug
│ │ debugfs
│ │ debugfs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/kernel/tracing
│ │ tracefs
│ │ tracefs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/fs/fuse/connections
│ │ fusectl
│ │ fusectl
│ │ rw,nosuid,nodev,noexec,relatime
│ └─/sys/kernel/config
│ configfs
│ configfs
│ rw,nosuid,nodev,noexec,relatime
├─/dev devtmpfs
│ devtmpfs
│ rw,nosuid,size=4096k,nr_inodes=1048576,mode=755,inode64
│ ├─/dev/shm
│ │ tmpfs tmpfs rw,nosuid,nodev,inode64
│ ├─/dev/pts
│ │ devpts devpts rw,nosuid,noexec,relatime,gid=5,mode=620,ptmxmode=000
│ ├─/dev/mqueue
│ │ mqueue mqueue rw,nosuid,nodev,noexec,relatime
│ └─/dev/hugepages
│ hugetlbfs
│ hugetlbfs
│ rw,relatime,pagesize=2M
├─/run tmpfs tmpfs rw,nosuid,nodev,size=4859812k,nr_inodes=819200,mode=755,inode64
│ ├─/run/user/1000
│ │ tmpfs tmpfs rw,nosuid,nodev,relatime,size=2429904k,nr_inodes=607476,mode=700,uid=1000,gid=100,inode64
│ │ ├─/run/user/1000/doc
│ │ │ portal fuse.portal
│ │ │ rw,nosuid,nodev,relatime,user_id=1000,group_id=100
│ │ └─/run/user/1000/gvfs
│ │ gvfsd-fuse
│ │ fuse.gvfsd-fuse
│ │ rw,nosuid,nodev,relatime,user_id=1000,group_id=100
│ └─/run/user/1002
│ tmpfs tmpfs rw,nosuid,nodev,relatime,size=2429904k,nr_inodes=607476,mode=700,uid=1002,gid=100,inode64
│ ├─/run/user/1002/doc
│ │ portal fuse.portal
│ │ rw,nosuid,nodev,relatime,user_id=1002,group_id=100
│ └─/run/user/1002/gvfs
│ gvfsd-fuse
│ fuse.gvfsd-fuse
│ rw,nosuid,nodev,relatime,user_id=1002,group_id=100
├─/home
│ /dev/nvme0n1p5
│ ext4 rw,relatime,data=ordered
├─/dati
│ /dev/nvme0n1p8
│ fuseblk
│ rw,nosuid,nodev,noexec,relatime,user_id=0,group_id=0,default_permissions,allow_other,blksize=4096
├─/boot/efi
│ /dev/nvme0n1p1
│ vfat rw,relatime,fmask=0022,dmask=0022,codepage=437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro
└─/tmp/.mount_ObsidiW6jN44
Obsidian-1.4.16.AppImage
fuse.Obsidian-1.4.16.AppImage
ro,nosuid,nodev,relatime,user_id=1000,group_id=100
pla@localhost:~>
=====================================================================
attached again in user pla and it works now
pla@localhost:~> findmnt -u
TARGET SOURCE FSTYPE OPTIONS
/ /dev/nvme0n1p4
│ ext4 rw,relatime
├─/proc
│ proc proc rw,nosuid,nodev,noexec,relatime
│ └─/proc/sys/fs/binfmt_misc
│ systemd-1
│ autofs rw,relatime,fd=30,pgrp=1,timeout=0,minproto=5,maxproto=5,direct,pipe_ino=24260
├─/sys sysfs sysfs rw,nosuid,nodev,noexec,relatime
│ ├─/sys/kernel/security
│ │ securityfs
│ │ securityfs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/fs/cgroup
│ │ tmpfs tmpfs ro,nosuid,nodev,noexec,size=4096k,nr_inodes=1024,mode=755,inode64
│ │ ├─/sys/fs/cgroup/unified
│ │ │ cgroup2
│ │ │ cgroup2
│ │ │ rw,nosuid,nodev,noexec,relatime,nsdelegate
│ │ ├─/sys/fs/cgroup/systemd
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,xattr,name=systemd
│ │ ├─/sys/fs/cgroup/misc
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,misc
│ │ ├─/sys/fs/cgroup/freezer
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,freezer
│ │ ├─/sys/fs/cgroup/blkio
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,blkio
│ │ ├─/sys/fs/cgroup/cpu,cpuacct
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,cpu,cpuacct
│ │ ├─/sys/fs/cgroup/rdma
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,rdma
│ │ ├─/sys/fs/cgroup/memory
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,memory
│ │ ├─/sys/fs/cgroup/net_cls,net_prio
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,net_cls,net_prio
│ │ ├─/sys/fs/cgroup/devices
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,devices
│ │ ├─/sys/fs/cgroup/perf_event
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,perf_event
│ │ ├─/sys/fs/cgroup/pids
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,pids
│ │ ├─/sys/fs/cgroup/hugetlb
│ │ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,hugetlb
│ │ └─/sys/fs/cgroup/cpuset
│ │ cgroup cgroup rw,nosuid,nodev,noexec,relatime,cpuset
│ ├─/sys/fs/pstore
│ │ pstore pstore rw,nosuid,nodev,noexec,relatime
│ ├─/sys/firmware/efi/efivars
│ │ efivarfs
│ │ efivarfs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/fs/bpf
│ │ bpf bpf rw,nosuid,nodev,noexec,relatime,mode=700
│ ├─/sys/kernel/debug
│ │ debugfs
│ │ debugfs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/kernel/tracing
│ │ tracefs
│ │ tracefs
│ │ rw,nosuid,nodev,noexec,relatime
│ ├─/sys/fs/fuse/connections
│ │ fusectl
│ │ fusectl
│ │ rw,nosuid,nodev,noexec,relatime
│ └─/sys/kernel/config
│ configfs
│ configfs
│ rw,nosuid,nodev,noexec,relatime
├─/dev devtmpfs
│ devtmpfs
│ rw,nosuid,size=4096k,nr_inodes=1048576,mode=755,inode64
│ ├─/dev/shm
│ │ tmpfs tmpfs rw,nosuid,nodev,inode64
│ ├─/dev/pts
│ │ devpts devpts rw,nosuid,noexec,relatime,gid=5,mode=620,ptmxmode=000
│ ├─/dev/mqueue
│ │ mqueue mqueue rw,nosuid,nodev,noexec,relatime
│ └─/dev/hugepages
│ hugetlbfs
│ hugetlbfs
│ rw,relatime,pagesize=2M
├─/run tmpfs tmpfs rw,nosuid,nodev,size=4859812k,nr_inodes=819200,mode=755,inode64
│ ├─/run/media/pla/backup7
│ │ /dev/sda1
│ │ fuseblk
│ │ rw,nosuid,nodev,relatime,user_id=0,group_id=0,default_permissions,allow_other,blksize=4096
│ ├─/run/user/1000
│ │ tmpfs tmpfs rw,nosuid,nodev,relatime,size=2429904k,nr_inodes=607476,mode=700,uid=1000,gid=100,inode64
│ │ ├─/run/user/1000/doc
│ │ │ portal fuse.portal
│ │ │ rw,nosuid,nodev,relatime,user_id=1000,group_id=100
│ │ └─/run/user/1000/gvfs
│ │ gvfsd-fuse
│ │ fuse.gvfsd-fuse
│ │ rw,nosuid,nodev,relatime,user_id=1000,group_id=100
│ └─/run/user/1002
│ tmpfs tmpfs rw,nosuid,nodev,relatime,size=2429904k,nr_inodes=607476,mode=700,uid=1002,gid=100,inode64
│ ├─/run/user/1002/doc
│ │ portal fuse.portal
│ │ rw,nosuid,nodev,relatime,user_id=1002,group_id=100
│ └─/run/user/1002/gvfs
│ gvfsd-fuse
│ fuse.gvfsd-fuse
│ rw,nosuid,nodev,relatime,user_id=1002,group_id=100
├─/home
│ /dev/nvme0n1p5
│ ext4 rw,relatime,data=ordered
├─/dati
│ /dev/nvme0n1p8
│ fuseblk
│ rw,nosuid,nodev,noexec,relatime,user_id=0,group_id=0,default_permissions,allow_other,blksize=4096
├─/boot/efi
│ /dev/nvme0n1p1
│ vfat rw,relatime,fmask=0022,dmask=0022,codepage=437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro
└─/tmp/.mount_ObsidiW6jN44
Obsidian-1.4.16.AppImage
fuse.Obsidian-1.4.16.AppImage
ro,nosuid,nodev,relatime,user_id=1000,group_id=100
pla@localhost:~>
Is it your USB disk? In this case it is mounted as shared and should be accessible by all users. What exact error do you get when you say that another user cannot access it?
I can:
erlangen:~ # cat /etc/udev/rules.d/99-udisks2.rules
# UDISKS_FILESYSTEM_SHARED
# ==1: mount filesystem to a shared directory (/media/VolumeName)
# ==0: mount filesystem to a private directory (/run/media/$USER/VolumeName)
# See udisks(8)
ENV{ID_FS_USAGE}=="filesystem|other|crypto", ENV{UDISKS_FILESYSTEM_SHARED}="1"
erlangen:~ #
The user mounting the device is owner and is granted write access. Others have read access.
erlangen:~ # findmnt /media/0050-E47F
TARGET SOURCE FSTYPE OPTIONS
/media/0050-E47F /dev/sdb1 vfat rw,nosuid,nodev,relatime,uid=1000,gid=100,fmask=0022,dmask=0022,codepage=437,iocharset=iso8859-1,shortname=mixed,showexec,utf8,flush,errors=remount-ro
erlangen:~ #
I attach my USB disk backup7 and access it in user pla6ST
I switch to user pla
if I try to access with dophin it gives a red band with this error:
Could not enter folder /run/media/pla6ST/backup7.
manythanks, so I should create a new rule in /etc/udev/rules.d?
and is it possible to have write access for all users?
[quote=“pier_andreit, post:13, topic:170890”]
manythanks, so I should create a new rule in /etc/udev/rules.d?[/quote]
Yep. Mounting is performed by udisks2.service.
Presumably you need to tell polkit. The following grants user karl permission to start dup.service (zypper dist-upgrade):
erlangen:~ # cat /etc/polkit-1/rules.d/00-dup.rules
// Allow karl to manage dup.service;
// fall back to implicit authorization otherwise.
polkit.addRule(function(action, subject) {
if (action.id == "org.freedesktop.systemd1.manage-units" &&
action.lookup("unit") == "dup.service" &&
subject.user == "karl") {
return polkit.Result.YES;
}
});
erlangen:~ #
OK, I was wrong, you have per-user mounts. You also apparently have NTFS filesystem on this USB disk and use ntfs-3g so we do not see mount options, passed during mount - we see FUSE mount options, which are not really interesting here. The output of
ps -wwef | grep ntfs
would be interesting.
Anyway - as far as I can tell, if you configure shared filesystem and try to mount NTFS via ntfs-3g, it is mounted as read-write for everyone by default. It is possible that KDE is using different options, in which case we need the output of the above command.
Create udev rule as instructed and do not forget to create /media directory which does not exist by default. Reboot and try again. If you have an error accessing this disk, show the output of the above command.
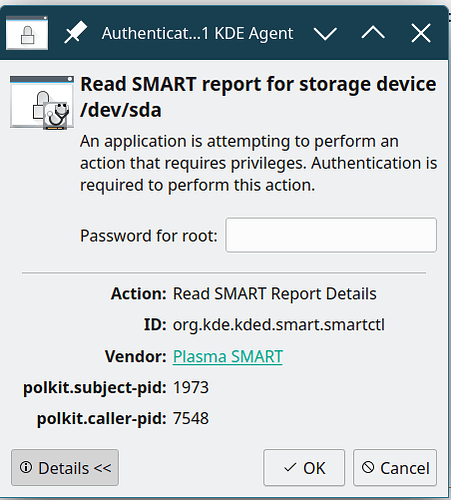
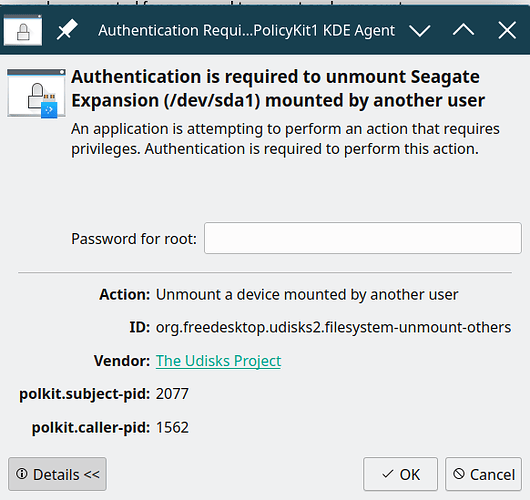
manythanks it works, but if I attach to user pla and access to USB disk, then switch to user pla6ST and access to the USB disk I receive this request:
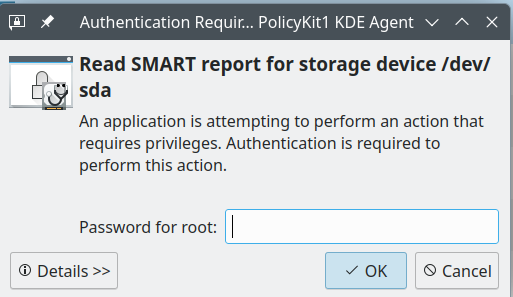
and when I try to safely remove this request:
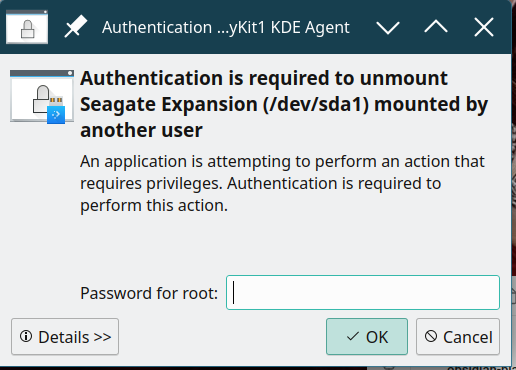
I would like to non be requested for password to mount and unmount,
reading what you suggested me I suppose to have to change something in:
/etc/polkit-default-privs.local
but I don’t know what, I suppose one of these:
org.freedesktop.udisks2.filesystem-mount
org.freedesktop.udisks2.filesystem-mount-other-seat
org.freedesktop.udisks2.filesystem-mount-system
for mount without password request
and this to unmount with password request
org.freedesktop.udisks2.filesystem-unmount-others
setting permission as
auth_admin:yes:yes
is this correct to allow any user to mount and unmount USB disks without password request?
or there is a better way you can suggest me?
Did you try to press “Details” on the authentication dialogue?
Udisks2 uses /usr/share/polkit-1/actions/org.freedesktop.UDisks2.policy. You may override these definitions in /etc/polkit-1/actions/.
http://storaged.org/doc/udisks2-api/latest/mount_options.html
So here you have action IDs for which you need to change permissions.