I am proud to announce my latest creation I call S.A.F.P. for SUSE Automated File Permissions. At its heart, it is a file listing program using the ls -l terminal command, but its purpose is to convert the normal file permissions string of rwxrwxrwx into a chmod number and back again. In the example file display above we are looking at the /boot/grub folder. I would get a similar list with the terminal command **ls -l /boot **but notice the (###) which shows the equivalent chmod number. S.A.F.P. can now creates KDE icon files on your desktop and in the Applications menu if allowed to. New settings for for icon file creation have been added.
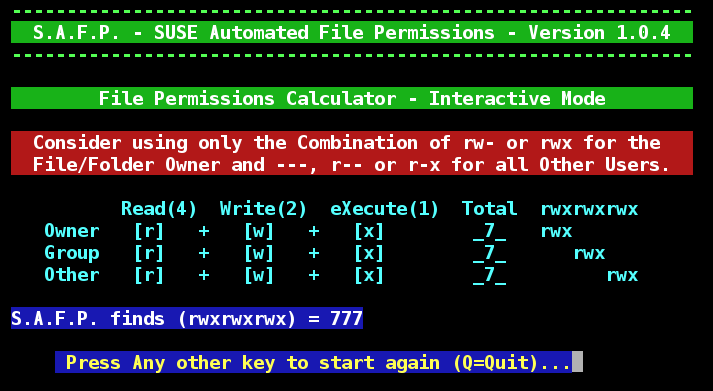
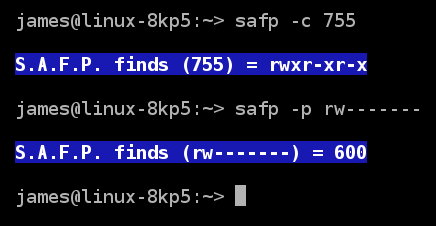
The terminal command chmod is used to change file mode bits and S.A.F.P. helps determine the correct number to be used. In addition to including the chmod number for each file and folder shown, you can use S.A.F.P. as a small chmod number calculator as shown below. Just use the permissions calculator mode safp -c ### to get the permission string or the safp -p rwxrwxrwx to get the chmod ###.
Or you can use the new Interactive Calculator mode in S.A.F.P. by using the safp -i command:
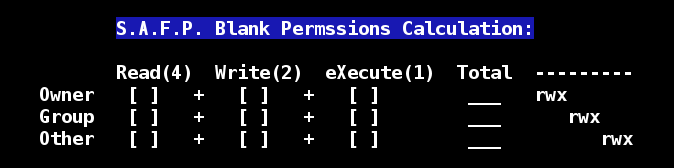
I have also added a blank Calculator you could print out and keep somewhere if you like. Use safp -b to obtain this screen below:
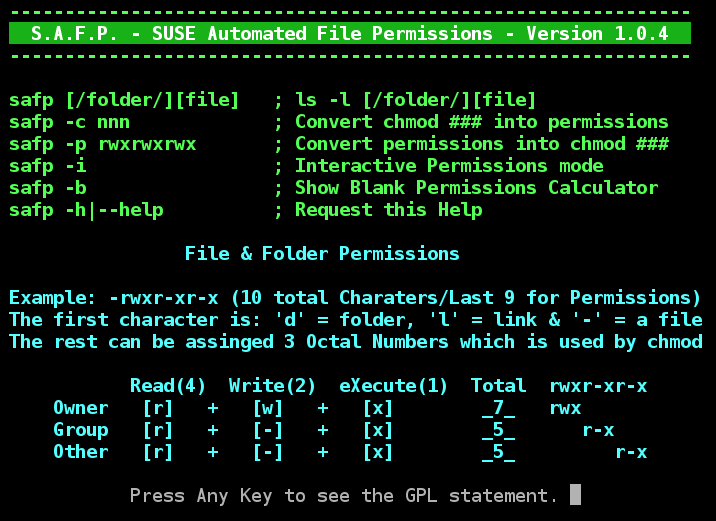
To get a full help listing just use the safp -h help request and get the next display shown below.
In order to start using the safp new file permissions helper, just Copy and Paste the text of this script into a text editor and save it as the file safp in your home area bin folder (~/bin/safp). The script is too large to be posted in a message here and is included in SUSE Paste.
S.A.F.P. - SUSE Automated File Permissions - Version 1.0.4
Open the above Link in a new Tab. Select the Download option in the top right and then select Open With Kwrite or other text editor and then save the bash script text file as ~/bin/safp. It is possible to directly download safp using the following terminal command (You must delete or remove the old version first):
rm ~/bin/safp
wget -nc http://paste.opensuse.org/view/download/29253557 -O ~/bin/safp
This script must be marked executable to be used. Please run the following Terminal command:
chmod +x ~/bin/safp
It is even possible to string all three of these commands together as one which is Highly Recommended for you to use! Copy the following command, open up a terminal session, paste it in and press enter:
rm ~/bin/safp ; wget -nc http://paste.opensuse.org/view/download/29253557 -O ~/bin/safp ; chmod +x ~/bin/safp
To use safp, open up a terminal session and type in the command:
safp
OR for help:
safp -h
To look at large folders of data, consider using the terminal less command. Once using less, use the ‘q’ command to quit. For instance, try this terminal command:
safp /etc | less
Chmod and the mysterious first octet
It has been pointed out to me that I should include info on the setuid, setgid and sticky bit settings. S.A.F.P. - SUSE Automated File Permissions, ignores these three bits in this example. For completeness, this is their meaning.
The chmod number actually includes four octal digits, not just three, but generally, the front & fourth digit is zero as in 0777. The weight of this front (first) number is as follows:
4 - setuid (letter-style: s, displayed the added letter s, i.e. -rwsrwxrwx)
2 - setgid (letter-style: s, displayed the added letter s, i.e. -rwxr-s—)
1 - sticky bit (letter-style: t, displayed the added letter s, i.e. drwxrwxrwt)
The meaning of these bits is said to mean:
**Setuid and Setgid Bits **
chmod clears the set-group-ID bit of a regular file if the file’s group ID does not match the user’s effective group ID or one of the user’s supplementary group IDs, unless the user has appropriate privileges. Additional restrictions may cause the set-user-ID and set-group-ID bits of MODE or RFILE to be ignored. This behavior depends on the policy and functionality of the underlying chmod system call. When in doubt, check the underlying system behavior.
chmod preserves a directory’s set-user-ID and set-group-ID bits unless you explicitly specify otherwise. You can set or clear the bits with symbolic modes like u+s and g-s, and you can set (but not clear) the bits with a numeric mode.
Restricted Deletion Flag or Sticky Bit
The restricted deletion flag or sticky bit is a single bit, whose interpretation depends on the file type. For directories, it prevents unprivileged users from removing or renaming a file in the directory unless they own the file or the directory; this is called the restricted deletion flag for the directory, and is commonly found on world-writable directories like /tmp. For regular files on some older systems, the bit saves the program’s text image on the swap device so it will load more quickly when run; this is called the sticky bit.
**A setuid, setgid and sticky bit Example: **
This link speaks of their possible usages: 🤠 Major Hayden, but be careful what you use them for!
If you have any questions or comments about the usage of S.A.F.P. - SUSE Automated File Permissions, please let me know.
Thank You for using openSUSE,
Blogs: asroot : Bash : Packet Filter : C.F.U. : GPU’s : fewrup : F.S.M. : H.I. : nVIDIA : LNVHW : N.S.F. : S.A.K.C. : MMCHECK
S.A.S.I. : S.C.L.U. : S.G.T.B. : S.K.I.M. : S.L.A.V.E. : S.L.R.C. : S.T.A.R.T. : S.U.F.F. : SYSEdit : systemd : YaST Power