ajgp
April 19, 2024, 4:27pm
1
Hi,
I am having what can only be described as one of the most irritating boot issues going!
I installed Opensuse Tumbleweed with secure boot enabled (TPM disabled) on my PC, absolutely no problem all went well and I booted via the opensuse-secureboot GRUB menu.
Roll on the next day, I powered on the computer and I am now getting SHIM errors when trying to boot; disable secure boot in BIOS and it now boots.
Next day, power on machine (with secure boot off) machine now fails to boot as it claims initramfs is corrupt (failed to extract); rebooot to BIOS, enable Secure Boot, and now machine boots.
Repeat the above cycle of having to enable/disable secure boot ad infinitum! (Separate boots do not have to be on consequtive days can just be spread over the day)
Hardware:
TPM is disabled in BIOS as with that enabled it never boots.
Possibly because, there was a new UEFI certificate issued for the Kernel.
With the user “root”, take a look in ‘/etc/uefi/certs/’ and, take note of the timestamp for each “.crt” file there.
# mokutil --import ?????.crt
You’ll be asked for a password.
If you’re non-USA, choose a simple password which only contains characters on YOUR keyboard which are the same as those – with the same physical position – on a US-ASCII keyboard.
Then execute –
# mokutil --password
to set up the utility’s initial password at reboot.
Reboot.
Before the UEFI/BIOS screen appears, you should be presented with a blue MokUtil screen – which times out if you aren’t fast enough …
Be quick – type in the password you setup before the reboot.
Then, choose to enroll the new MOK Key and, follow the instructions on the screen.
ajgp
April 19, 2024, 5:44pm
3
does secure boot need to be enabled when i run the mok-util does it need to be from a secure-boot session or can I be booted into Tumbleweed with secure boot disabled to do it?
Im assuming im looking for the newest cert to use
ajgp
April 19, 2024, 6:06pm
4
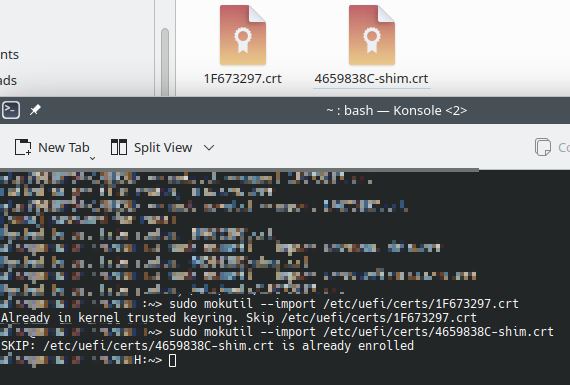
OK so I tried that, I only have 2 certs in the /etc/uefi/certs folder and when I try to run mokutil I get told they are already trusted / enrolled
Welcome, have you installed any drivers by any chance? If you install drivers from external repositories, they are unsigned, so either sign them or disable secure boot.
ajgp
April 19, 2024, 7:33pm
6
I have installed printer drivers from HP; however this issue pre-dates that installation and I havent added anything else out of repo driver wise.
Here with Leap 15.5 but, for Tumbleweed possibly almost the same –
You need at least the following packages for Trusted Platform Module (TPM) support:
# LANG=C zypper search --installed-only TPM
Loading repository data...
Reading installed packages...
S | Name | Summary | Type
---+--------------+-------------------------------------------------------------------------------+--------
i | libtpms0 | Library providing Trusted Platform Module (TPM) functionality | package
i | tpm2-0-tss | Intel's TCG Software Stack access libraries for TPM 2.0 chips | package
i | tpm2.0-abrmd | Intel's TCG Software Stack Access Broker & Resource Manager for TPM 2.0 chips | package
i+ | tpm2.0-tools | Trusted Platform Module (TPM) 2.0 administration tools | package
#
Then you’ll have to check the systemd Journal – here on Leap 15.5 with Secure Boot and TPM enabled –
# journalctl -b 0 --no-hostname --output=short-monotonic --system | grep -iE 'secur|cert|tpm|spect'[ 0.000000] kernel: Command line: BOOT_IMAGE=/boot/vmlinuz-5.14.21-150500.55.52-default root=UUID=c59a64bf-b464-4ea2-bf3a-d3fd9dded03f splash=silent resume=/dev/disk/by-id/ata-Intenso_SSD_Sata_III_AA000000000000035990-part3 quiet tsc=unstable security=apparmor mitigations=auto
[ 0.000000] kernel: efi: ACPI=0xca831000 ACPI 2.0=0xca831014 TPMFinalLog=0xcab8a000 SMBIOS=0xcb9f4000 SMBIOS 3.0=0xcb9f3000 MEMATTR=0xc8b25818 ESRT=0xc95e6598 MOKvar=0xcba51000 RNG=0xca813c18 TPMEventLog=0xc14fc018
[ 0.000000] kernel: secureboot: Secure boot enabled
[ 0.000000] kernel: Kernel is locked down from EFI Secure Boot mode; see man kernel_lockdown.7
[ 0.004989] kernel: secureboot: Secure boot enabled
[ 0.005048] kernel: ACPI: TPM2 0x00000000CA724000 00004C (v04 ALASKA A M I 00000001 AMI 00000000)
[ 0.005094] kernel: ACPI: Reserving TPM2 table memory at [mem 0xca724000-0xca72404b]
[ 0.019309] kernel: Kernel command line: BOOT_IMAGE=/boot/vmlinuz-5.14.21-150500.55.52-default root=UUID=c59a64bf-b464-4ea2-bf3a-d3fd9dded03f splash=silent resume=/dev/disk/by-id/ata-Intenso_SSD_Sata_III_AA000000000000035990-part3 quiet tsc=unstable security=apparmor mitigations=auto
[ 0.100482] kernel: Spectre V1 : Mitigation: usercopy/swapgs barriers and __user pointer sanitization
[ 0.100484] kernel: Spectre V2 : Mitigation: Retpolines
[ 0.100484] kernel: Spectre V2 : Spectre v2 / SpectreRSB mitigation: Filling RSB on context switch
[ 0.100485] kernel: Spectre V2 : Spectre v2 / SpectreRSB : Filling RSB on VMEXIT
[ 0.100485] kernel: Spectre V2 : Enabling Speculation Barrier for firmware calls
[ 0.100488] kernel: Spectre V2 : mitigation: Enabling conditional Indirect Branch Prediction Barrier
[ 0.122120] kernel: LSM: Security Framework initializing
[ 1.025486] kernel: Loading compiled-in X.509 certificates
[ 1.025520] kernel: Loaded X.509 cert 'SUSE Linux Enterprise Secure Boot Signkey: a746b64b6cb71f13385638055f46162bac632acd'
[ 1.029474] kernel: integrity: Loading X.509 certificate: UEFI:db
[ 1.052625] kernel: integrity: Loaded X.509 cert 'ASUSTeK MotherBoard SW Key Certificate: da83b990422ebc8c441f8d8b039a65a2'
[ 1.052628] kernel: integrity: Loading X.509 certificate: UEFI:db
[ 1.052845] kernel: integrity: Loaded X.509 cert 'ASUSTeK Notebook SW Key Certificate: b8e581e4df77a5bb4282d5ccfc00c071'
[ 1.052847] kernel: integrity: Loading X.509 certificate: UEFI:db
[ 1.052874] kernel: integrity: Loaded X.509 cert 'Microsoft Corporation UEFI CA 2011: 13adbf4309bd82709c8cd54f316ed522988a1bd4'
[ 1.052876] kernel: integrity: Loading X.509 certificate: UEFI:db
[ 1.052902] kernel: integrity: Loaded X.509 cert 'Microsoft Windows Production PCA 2011: a92902398e16c49778cd90f99e4f9ae17c55af53'
[ 1.052904] kernel: integrity: Loading X.509 certificate: UEFI:db
[ 1.053119] kernel: integrity: Loaded X.509 cert 'Canonical Ltd. Master Certificate Authority: ad91990bc22ab1f517048c23b6655a268e345a63'
[ 1.053313] kernel: integrity: Loading X.509 certificate: UEFI:MokListRT (MOKvar table)
[ 1.053538] kernel: integrity: Loaded X.509 cert 'SUSE Linux Enterprise Secure Boot CA: ecab0d42c456cf770436b973993862965e87262f'
[ 1.053540] kernel: integrity: Loading X.509 certificate: UEFI:MokListRT (MOKvar table)
[ 1.053569] kernel: integrity: Loaded X.509 cert 'openSUSE Secure Boot Signkey: fd9f2c12e599d67cc7f9067541adf426b712469e'
[ 1.053577] kernel: Loading compiled-in module X.509 certificates
[ 1.053601] kernel: Loaded X.509 cert 'SUSE Linux Enterprise Secure Boot Signkey: a746b64b6cb71f13385638055f46162bac632acd'
[ 1.200744] kernel: evm: security.selinux
[ 1.200748] kernel: evm: security.SMACK64 (disabled)
[ 1.200752] kernel: evm: security.SMACK64EXEC (disabled)
[ 1.200755] kernel: evm: security.SMACK64TRANSMUTE (disabled)
[ 1.200759] kernel: evm: security.SMACK64MMAP (disabled)
[ 1.200762] kernel: evm: security.apparmor
[ 1.200765] kernel: evm: security.ima
[ 1.200768] kernel: evm: security.capability
[ 1.238001] systemd[1]: systemd 249.17+suse.218.g2cb4d40f1c running in system mode (+PAM +AUDIT +SELINUX +APPARMOR -IMA -SMACK +SECCOMP +GCRYPT +GNUTLS +OPENSSL +ACL +BLKID +CURL +ELFUTILS +FIDO2 +IDN2 -IDN +IPTC +KMOD +LIBCRYPTSETUP +LIBFDISK +PCRE2 +PWQUALITY +P11KIT +QRENCODE +TPM2 +BZIP2 +LZ4 +XZ +ZLIB +ZSTD -XKBCOMMON +UTMP +SYSVINIT default-hierarchy=hybrid)
[ 1.463749] dracut-cmdline[244]: Using kernel command line parameters: root=UUID=c59a64bf-b464-4ea2-bf3a-d3fd9dded03f rootfstype=ext4 rootflags=rw,noatime BOOT_IMAGE=/boot/vmlinuz-5.14.21-150500.55.52-default root=UUID=c59a64bf-b464-4ea2-bf3a-d3fd9dded03f splash=silent resume=/dev/disk/by-id/ata-Intenso_SSD_Sata_III_AA000000000000035990-part3 quiet tsc=unstable security=apparmor mitigations=auto
[ 1.647444] plymouthd[354]: 00:00:01.644 ply-utils.c:946:ply_get_kernel_command_line : Kernel command line is: 'BOOT_IMAGE=/boot/vmlinuz-5.14.21-150500.55.52-default root=UUID=c59a64bf-b464-4ea2-bf3a-d3fd9dded03f splash=silent resume=/dev/disk/by-id/ata-Intenso_SSD_Sata_III_AA000000000000035990-part3 quiet tsc=unstable security=apparmor mitigations=auto
[ 5.852567] systemd[1]: systemd 249.17+suse.218.g2cb4d40f1c running in system mode (+PAM +AUDIT +SELINUX +APPARMOR -IMA -SMACK +SECCOMP +GCRYPT +GNUTLS +OPENSSL +ACL +BLKID +CURL +ELFUTILS +FIDO2 +IDN2 -IDN +IPTC +KMOD +LIBCRYPTSETUP +LIBFDISK +PCRE2 +PWQUALITY +P11KIT +QRENCODE +TPM2 +BZIP2 +LZ4 +XZ +ZLIB +ZSTD -XKBCOMMON +UTMP +SYSVINIT default-hierarchy=hybrid)
[ 6.505726] systemd[1]: Found device /dev/tpm0.
[ 6.894469] plymouthd[851]: 00:00:06.894 ply-utils.c:946:ply_get_kernel_command_line : Kernel command line is: 'BOOT_IMAGE=/boot/vmlinuz-5.14.21-150500.55.52-default root=UUID=c59a64bf-b464-4ea2-bf3a-d3fd9dded03f splash=silent resume=/dev/disk/by-id/ata-Intenso_SSD_Sata_III_AA000000000000035990-part3 quiet tsc=unstable security=apparmor mitigations=auto
[ 6.900589] kernel: SGI XFS with ACLs, security attributes, quota, no debug enabled
[ 8.777471] systemd[1]: Starting Security Auditing Service...
[ 8.783326] systemd[1]: Condition check resulted in RPC security service for NFS client and server being skipped.
[ 8.783491] systemd[1]: Condition check resulted in RPC security service for NFS server being skipped.
[ 8.863578] systemd[1]: Started Security Auditing Service.
[ 8.881910] systemd[1]: Started Watch for changes in CA certificates.
[ 8.936110] systemd[1]: Starting TPM2 Access Broker and Resource Management Daemon...
[ 9.021640] tpm2-abrmd[1036]: tcti_conf before: "(null)"
[ 9.022093] tpm2-abrmd[1036]: tcti_conf after: "device:/dev/tpm0"
[ 9.050954] systemd[1]: Started TPM2 Access Broker and Resource Management Daemon.
#
You need to check for the following items –
Certificates – Microsoft Certificates for UEFI.
The SUSE Secure Boot Key.
ajgp
April 24, 2024, 9:43pm
10
So I had upgraded my BIOS to the latest version from quite an old one which is when the boot issues started. The reason for upgrading was because I needed a newer BIOS version in order to install my new 5700X3D CPU once I replaced the CPU the boot issues appear to have gone away.
So problem appears to be related to the BIOS version and the CPU…
system
May 1, 2024, 9:44pm
11
This topic was automatically closed 7 days after the last reply. New replies are no longer allowed.