Hi, this is my first post here and I hope I chose the right form and keyword. I have a lot of experience with using and administrating comparatively “raw” Linuxes (Debian and Arch with XFCE), but recently I have started to favour openSUSE Tumbleweed with KDE as the Linux that hopefully I can give to for “non-technical” friends. In fact I’m quite enthusiastic about Tumbleweed/KDE. It looks beautiful, updates itself and should not require too much intervention from me – no need for distro upgrades every few years and well-curated “rolling” updates that will rarely break things. At least that’s my current impression. I have very little KDE experience but enjoyed playing with it on the two installations I did so far before giving them away. Of course RustDesk is part of these installations for any further support sessions.
For the second, more “serious” try I set up the end user’s personal account over this weekend and had the “handover” session today. I completed the setup while my pre-set login password was still in place and was going to ask my friend to take ownership by changing the user password as one of the final steps of the meeting. I had decided to use ecryptfs on this laptop – my preference had been full encryption via LUKS but regrettably that didn’t work; the boot password prompt appeared but the keyboard didn’t seem to work at that point. I didn’t take the time to investigate further.
I understand that ecryptfs has its drawbacks and was therefore not surprised that it wasn’t offered by the installer. I saw some online info (outdated perhaps) about ecryptfs setup being possible via YaST but couldn’t find this. So I set up ecryptfs via the ecryptfs-migrate-home command. Since I wanted to let my friend decide about encryption, I only did this during the handover meeting. So just like with LUKS over the weekend, I would not have the time to investigate any encryption problems in depth. I asked my friend to write down and store the key generated by ecryptfs-migrate-home, logged out and back in successfully, then rebooted to see that the encryption would automatically be unlocked, and it worked.
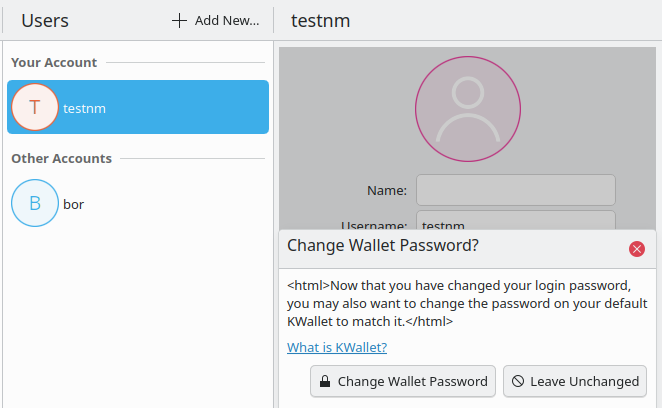
Then when the time came to change the login password, I was of course interested to see if the change would be propagated to ecryptfs. I therefore didn’t use any command line tools but the KDE user settings, hoping that KDE would know about any other components that are unlocked by the login password. That did not work. First I logged out and back in and saw that KDE wallet asked for a password, which I initially ignored. At least ecryptfs looked fine at that point. But when I then rebooted I saw that the password change had not been propagated. There were dozens of error dialogs about files not being writable (in fact they didn’t exist) and when logging in from the command line I could see that the home directory had been replaced by a dummy that helpfully contained a Readme file and a launcher with explanations how I could unlock the encryption (using the previous login password). I did that and then used ecryptfs-rewrap-passphrase to set the passphrase to the new login password. To complete the password change, I then changed the KDE wallet passphrase as well. After this, everything worked as it should even after a reboot. I was now able to hand over the laptop.
My question is: Is there a way to change the login password that will automatically update the password for the KDE wallet, and ideally also rewrap the ecryptfs passphrase?
Thanks for your thoughts.