I have been using Linux for 23 years and I have never had any problems. My security includes different strong passwords for both the root and users, only downloading software from openSUSE, installing patches and updates as soon as possible after they arrive, backing /home up on a weekly basis and storing the backup at a different physical location and not clicking on anything, whether in an email or on a website, which I am not sure about. Over recent years, most browsers and email clients in Linux will warn you if they suspect there is a problem.
Ok. But please tell me just one thing:
In old WinXP era I was using this good little tool:
https://www.softpedia.com/get/Security/Firewall/Sygate-Personal-Firewall-Free.shtml )
On
Linux there is nothing like this, that give me nice popups with block/allow buttons.
So things are much harder, and much more work.
So could I ask for any example (preferrably GUI way) how to confogure OpenSuse firewall to do this:
1.Block all programs incoming and outgoing co nections except one (eg. Firefox)
2.Block all exe’s runned by WINE from internet access
Neither of this is possible using standard kernel netfilter (which is what all Linux firewalls use). I could imagine something using network namespace, but there is no provision to run each command in separate namespace in openSUSE. You may look at Qubes which does run each command in separate environment and provides firewall settings for it. I do not know if it also implements interactive “open on request” popups.
@JanSpam,
IMHO you should try to re-think a lot of what you are after. Switching from Windows to Linux requires a complete fresh insight. The simple saying is: forget everything you know about computers and start anew.
Unix/Linux is a multi-user, multi-session operating system. Now that is easy to say, but it is not so easy to understand the consequences of this. It is far reaching.
E.g. talking about a “personal firewall” is confusing. Most people understand this a s a firewall on their “personal computer”. But in Unix/Linux “personal computer” is not a defined term. It is just the computer and it runs Unix/Linux. Hardware ranges from supercomputers in a data center to hand-held systems.
Yes, apart from the firewall that separates your LAN from to Internet, you also can have a firewall on your desktop/laptop/notebook with Linux. But it is something on the system level (and thus for all users) and not on the individual user level. Do you call that “personal”?
And remember that the system firewall on Linux is basically a real firewall that you can configure to let a system act as a “firewall”, complete with external, internal and demilitarized zones and port forwarding, etc. Usage on a desktop within a LAN is mostly only a subset from the features (just to allow some services and block others, incoming and outgoing).
And maybe you should get less “paranoic” as you call it. Most Linux users will not be very impressed by such a goal. I e.g. do not even run a firewall on my systems. I depend on the functionality of de firewall in my router and on the fact that I manage all the system in my LAN.
Also I (in my function as system manager) do not start network serving programs that are not needed, thus limiting the number of open ports. Also the few services used (ssh, rsync, …) have configurations that allow access only for limited IP addresses. Once done, not much to manage. Maybe check open ports every now and then.
IMHO you should try to understand what OP asks. It is very simple - prevent rogue program from silently accessing Internet, i.e. block outgoing connections by default except for some whitelisted programs. There is no need for preaching how far more advanced Linux is (which it is not) - just show how to do this very simple task.
I do not see how “personal” vs. “system” vs. “multi-user” is relevant here.
Here some continuation, when topic was accidenatly deleted:
Solution is to use user groups to block interent access.
It could be good, and I will try it, but it still not simple and friendly.
And now imagine yourself as 10 year children who just want to run online game, who is also admin of system and takes care about viruses (as I was with my XP machine 15 years ago ![]() ). What firewall is easier to learn for this child?
). What firewall is easier to learn for this child?
You dont’t like Windows, and Microsoft, I understand. They are spying, they are forcing strange interface solitions, and don’t let people decide, but they not always were so bad. Do You tried run Win95 on VM? Do you see the installer. It let user choose software, just like OpenSuse installer ![]() One of options was to keep Win3.1 interface…
One of options was to keep Win3.1 interface…
But takes look on Android. I was Android user before I first try Linux (this was Mint) I was dissaponited it don’t have program permissions like Android. Ok. Google is more awful company than MS. But apps permission system is very good idea. Even child can use it, if care about privacy & security. Btw. I have rooted and ungoogled smartphone.
I think Linux developers in future should think about something like program peemissions (but with option to block internet)
@JamSpam set up pihole in a container (I use a raspberry pi 3) and use that as the DNS https://pi-hole.net/ you can blacklist any site, not just an add blocker…
Or just use /etc/hosts to deny…
One of links in your other topics mentioned OpenSnitch; I do not know if it satisfies your requirements, but the first feature in README is “Interactive outbound connections filtering”. Looking in the documentation, rules may include
process.path(the path of the executable)process.idPIDprocess.command(full command line, including path and arguments)
and it has interactive popups “Whenever a process wants to establish a new connection, OpenSnitch will prompt you to allow or deny it”. Seems to do exactly what you want.
The following link may be of interest:
Ok. I will check this Opensnitch. Looks promising
But under Yast firewall config I just click public zone (which only allow dhcpv6) accept and it’s enough? Firewall is configured?
As I read SSH is something with remote desktop? So if it’s not in allowed list all remote attacks will be blocked?
IMO, the Firewalld GUI is a better utility. Install the “firewall-config” for that.
One of many articles to give you an overview…
Yes, if you have no need for it don’t permit it. In any case you probably don’t have sshd active…
systemctl status sshdOf course not. You probably need to step back (actually I suspect you need to take a lot of steps back) and define your threat model and what you are trying to defend against. Only then makes it sense to start looking for tools to do it.
I just asked to make sure. Installer default settings was to disable it.
On Windows remote desktop services was enabled by default.
Dealing with the 2nd wish first –
- No, but, you could block WINE from accessing the network – possibly – see below …
The 1st wish:
- You may, possibly, be able to use AppArmor to deny network access to specific applications:
<https://unix.stackexchange.com/questions/135115/apparmor-profile-deny-internet-access>
AppArmor Profile – add “#include <tunables/global>” to the top of each relevant Profile file, and then in each Profile for the applications to be denied Network access, include –
deny network inet,
deny network inet6,
deny network raw,
But, I’ve absolutely no idea if, the openSUSE Kernel will support this.
# aa-features-abi -x | grep 'network_v8' -B 1 -A 1
}
network_v8 {af_mask {unspec unix inet ax25 ipx appletalk netrom bridge atmpvc x25 inet6 rose netbeui security key netlink packet ash econet atmsvc rds sna irda pppox wanpipe llc ib mpls can tipc bluetooth iucv rxrpc isdn phonet ieee802154 caif alg nfc vsock kcm qipcrtr smc xdp
}
#
# aa-status
apparmor module is loaded.
67 profiles are loaded.
66 profiles are in enforce mode.
/usr/bin/lessopen.sh
/usr/lib/colord
/usr/lib/nagios/plugins/check_dhcp
/usr/lib/nagios/plugins/check_disk
/usr/lib/nagios/plugins/check_icmp
/usr/lib/nagios/plugins/check_ide_smart
/usr/lib/nagios/plugins/check_load
/usr/lib/nagios/plugins/check_ntp_time
/usr/lib/nagios/plugins/check_ping
/usr/lib/nagios/plugins/check_procs
/usr/lib/nagios/plugins/check_swap
/usr/lib/nagios/plugins/check_users
/usr/share/gitweb/gitweb.cgi
apache2
apache2//DEFAULT_URI
apache2//HANDLING_UNTRUSTED_INPUT
apache2//phpsysinfo
avahi-daemon
dnsmasq
dnsmasq//libvirt_leaseshelper
dovecot
dovecot-anvil
dovecot-auth
dovecot-config
dovecot-deliver
dovecot-dict
dovecot-dovecot-auth
dovecot-dovecot-lda
dovecot-dovecot-lda//sendmail
dovecot-imap
dovecot-imap-login
dovecot-lmtp
dovecot-log
dovecot-managesieve
dovecot-managesieve-login
dovecot-pop3
dovecot-pop3-login
dovecot-script-login
dovecot-ssl-params
dovecot-stats
identd
klogd
lsb_release
mdnsd
nmbd
nscd
ntpd
nvidia_modprobe
nvidia_modprobe//kmod
php-fpm
ping
samba-bgqd
samba-dcerpcd
samba-rpcd
samba-rpcd-classic
samba-rpcd-spoolss
smbd
smbldap-useradd
smbldap-useradd///etc/init.d/nscd
syslog-ng
syslogd
traceroute
winbindd
zgrep
zgrep//helper
zgrep//sed
1 profiles are in complain mode.
/usr/lib/nagios/plugins/check_ssh
0 profiles are in kill mode.
0 profiles are in unconfined mode.
3 processes have profiles defined.
3 processes are in enforce mode.
/usr/lib/colord (1854)
/usr/sbin/avahi-daemon (977) avahi-daemon
/usr/sbin/nscd (1015) nscd
0 processes are in complain mode.
0 processes are unconfined but have a profile defined.
0 processes are in mixed mode.
0 processes are in kill mode.
#
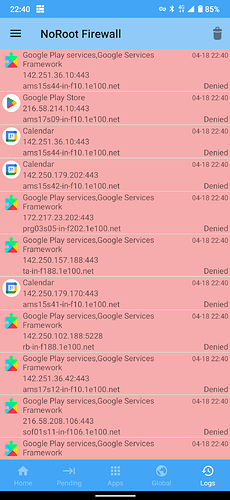
I am running such a firewall on my Android phone, it is shocking to see how often Google want to phone home:
For some reason I did never think of running that for Linux as I think I know what is going on but yes checking is better than trusting. I saw there is also something for Linux:
Never tried it but I might give it a try.
I keep Win10Pro on a different SSD to remind me how good I have it with OSS 15.4: It’s the same differences between a truly free / democratic nation vs a communist country. As a novice who has used linux for over a decade, all the security of the 2nd amendment of the U.S. Constitution is there with only the borders that you can open (secure and insecure) including an idiot proof recovery system (system snapshots).
You can use openSUSE MicroOS to minimize the attack surface, as this system is immutable.
Run all you can inside containers (Docker, Podman, Flatpak). Run apps as a non-root user.
openSUSE packages have signatures, if someone wants to temper it, your package will have a broken signature. Don’t trust any signing keys you don’t know. Don’t add any repositories you do not trust. Don’t install random things.
Encrypt your drives with LUKS, if your device is stolen, your data is mostly safe.
You can use AdGuard Home, which is more friendly than PiHole. AdGuard blocks tracking and also some malware, but only at the DNS level.
You could also look into OPNsense, if you want a firewall for your network.
Avoid products from certain countries/companies, they all phone home.
i do this with every new install and add them to this file you will have to create. you can google to see what exactly they do. hope it helps
sudo nano /etc/sysctl.d/70-yast.conf
net.inet.tcp.rfc1323=0
net.inet.icmp.timestamp=0
vm.swappiness=0
kernel.randomize_va_space = 2
fs.suid_dumpable = 0
hard core 0
kernel.exec-shield = 1
net.ipv4.ip_forward = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.icmp_ignore_bogus_error_responses 1
also install things like
install
firejail
jondo
unbound
and use encrypted dns or atleast cloudflair and a trusted vpn like mullvad.
and maybe consider using a router with a custom firmware like dd-wrt or openwrt or tomato
I’ll save a google search. These settings either have nothing to do with security, or are set to their current default values or don’t even exist or belong on limits.conf.